Quantstamp: A Modern Deep Dive into Blockchain Security Audits & Best Practices
In a space where a single vulnerability can cost millions, Quantstamp’s audits help teams build safer protocols and earn investor trust. This guide translates their process into practical security habits you can apply today.
- Audit Scope and Standards
- Methodologies: Automated vs Manual Testing
- Vulnerability Reporting & Remediation
- Notable Projects Audited
- How Audits Help Identify & Mitigate Vulnerabilities
- Future of Blockchain Security
- Best Practices & Practical Checklist
- FAQ
Audit Scope and Standards
Quantstamp evaluates smart contracts, upgrade paths, and governance models against industry norms. Their scope adapts to project risk, from DeFi to NFT ecosystems. Public validation, like Reuters, reinforces confidence in the process. Pros include broad coverage; cons can involve longer timelines for very large systems.
Best-in-class checks
Key areas include access control, reentrancy, arithmetic safety, and upgrade safety. The framework can be complemented by backdoor risk awareness, ensuring defense-in-depth across design and deployment.
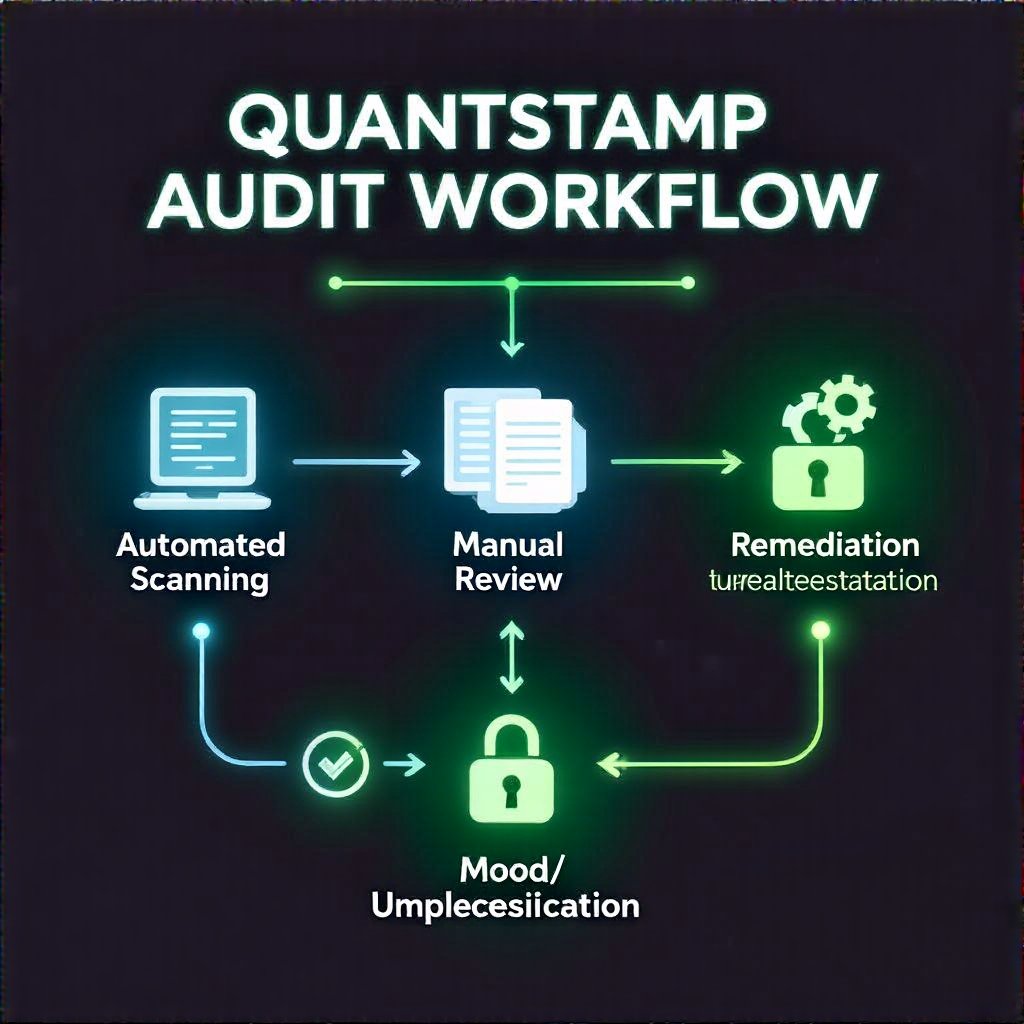
Methodologies: Automated vs Manual Testing
Quantstamp blends automated scanners with expert reviews. Automated tools catch common bugs; human reviewers spot edge cases and logical flaws that tools miss. This hybrid approach reduces blind spots and accelerates remediation.
Vulnerability Reporting & Remediation
Findings are delivered with a prioritized roadmap. Clear remediation steps help developers fix issues before launch, lowering post-deploy risk. For practical defense, study reentrancy patterns in reentrancy defenses.
Notable Projects Audited
Quantstamp has audited a wide range of DeFi and NFT platforms, contributing to safer launches. Public records and industry impact include prevented exploits and greater investor trust. Reuters coverage provides context for their scale and influence: Reuters.
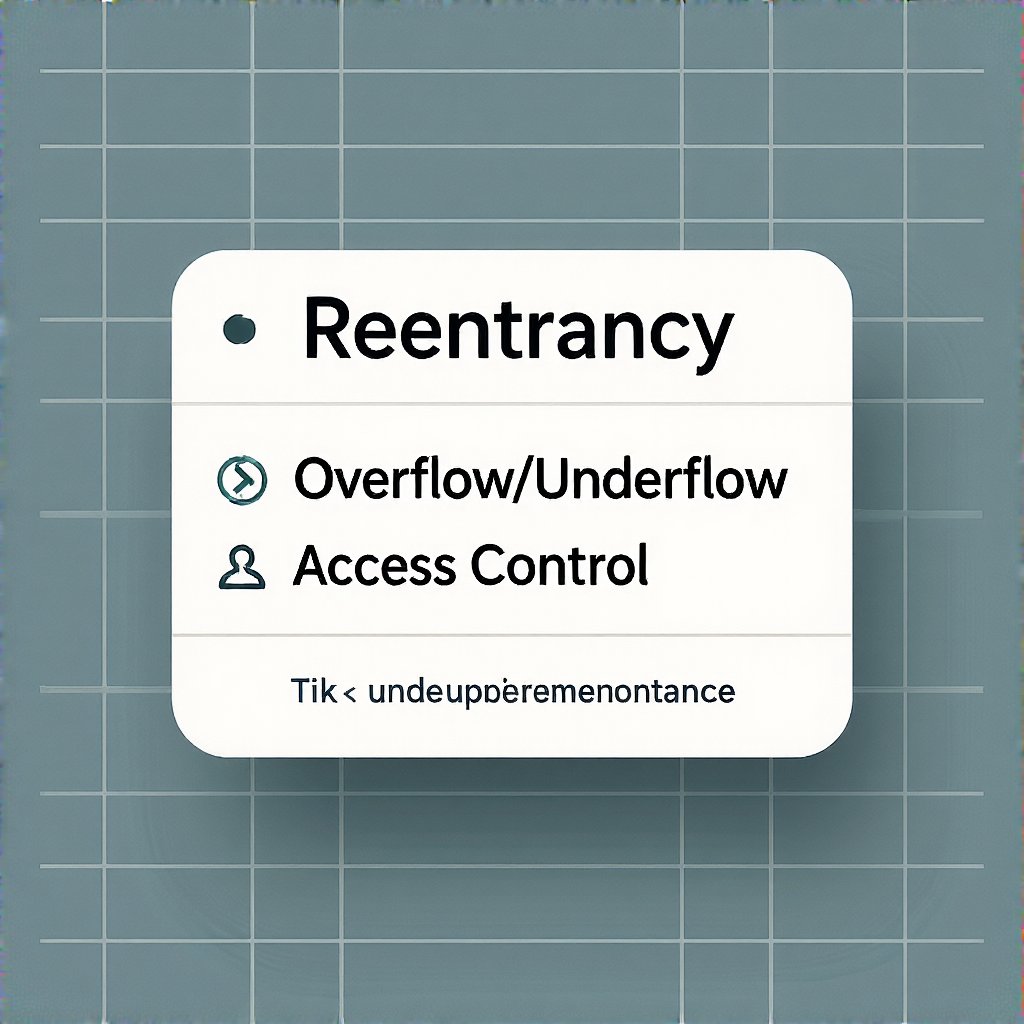
How Audits Help Identify & Mitigate Vulnerabilities
- Detection of reentrancy, overflow/underflow, and access-control gaps.
- Evaluation of logic flows for potential attack vectors.
- Evaluation against secure design patterns and standards.
Integrating these insights into your workflow matters. For instance, ensure robust vesting policies and disciplined liquidity controls to prevent manipulation; also align with launch-readiness steps in the Solana launch checklist.
Future of Blockchain Security
Threats evolve, and Quantstamp emphasizes ongoing education and proactive security culture. Their approach echoes the OWASP Top Ten and the standards set by national bodies like NIST (Secure Software Development).
Best Practices: Practical Security Checklist
A security-first mindset includes threat modeling in design, regular audits, and up-to-date dependency checks. Use this concise checklist to act quickly:
| Step | Action | Owner | Frequency |
|---|---|---|---|
| Plan | Incorporate threat modeling in design docs | CTO / Dev Lead | Per project |
| Test | Run automated scans + manual review | Security Engineer | On each release |
| Remediate | Apply fixes and re-test critical paths | Dev Team | As needed |
Following these steps helps teams move from detection to durable prevention, reducing risk across the project lifecycle.
FAQ
- What does Quantstamp audit cover?
- Smart contracts, governance, and upgrade paths.
- Why are audits essential for investors?
- Audits reduce risk and increase confidence before funding.
