Celer Network ($CELR) Review: A Data-Driven Look at Its Legitimacy, Technology, and Risks
What Is Celer Network: An Introduction
Celer Network is a blockchain infrastructure project focused on enabling fast, secure, and low-cost cross-chain interoperability. Its core goal is to build a scalable, multi-chain ecosystem that allows seamless communication, asset transfer, and shared states across heterogeneous blockchain networks. This review offers an impartial analysis of its technological foundation, community engagement, security posture, tokenomics, and potential risks.
Through products like cBridge, a multi-chain asset transfer solution, and Celer IM, an inter-chain messaging framework, Celer aims to simplify cross-chain interactions for developers and end-users. The project claims support for over 45 different chains and 175 tokens, positioning itself as a significant player in the blockchain interoperability space. This overview scrutinizes the project's legitimacy by examining its technical claims, audit results, community activity, and strategic partnerships.
The Team and Roadmap Evaluation
Based on publicly available information and community summaries, Celer Network boasts a highly qualified team comprising researchers with PhDs from top-tier universities such as MIT, UC Berkeley, Princeton, and UIUC, complemented by industry veterans from Google, Amazon, Alibaba, and other major tech firms. This stellar academic and professional pedigree suggests a strong technical foundation and a commitment to cutting-edge development.
While specific milestones from their roadmap are not exhaustively detailed here, their active product deployment—such as cBridge and Celer IM—and ongoing bug bounty programs indicate steady progress. The project's strategic partnerships with other blockchain initiatives and continuous product enhancements demonstrate capability and intent to deliver on ambitious goals. The team’s experience and active development cycles suggest a credible trajectory towards fulfillment of their promised features.
- Support for diverse blockchains including Layer 1s (Ethereum, BNB, Avalanche), Layer 2s (Optimism, zkEVM, Scroll), and emerging chains like Sui and Oasis.
- Launch of cBridge with continuous network integrations, broadening the ecosystem’s utility.
- Implementation of decentralized governance through community proposals (noted by extensive CIP discussions on forums).
- Active bug bounty and security initiatives, including partnerships with Immunefi and planned SGN security audits.
Overall, the team’s background, combined with visible technological developments, supports a credible ability to deliver on future milestones, although risks remain if execution falters or if security vulnerabilities emerge.
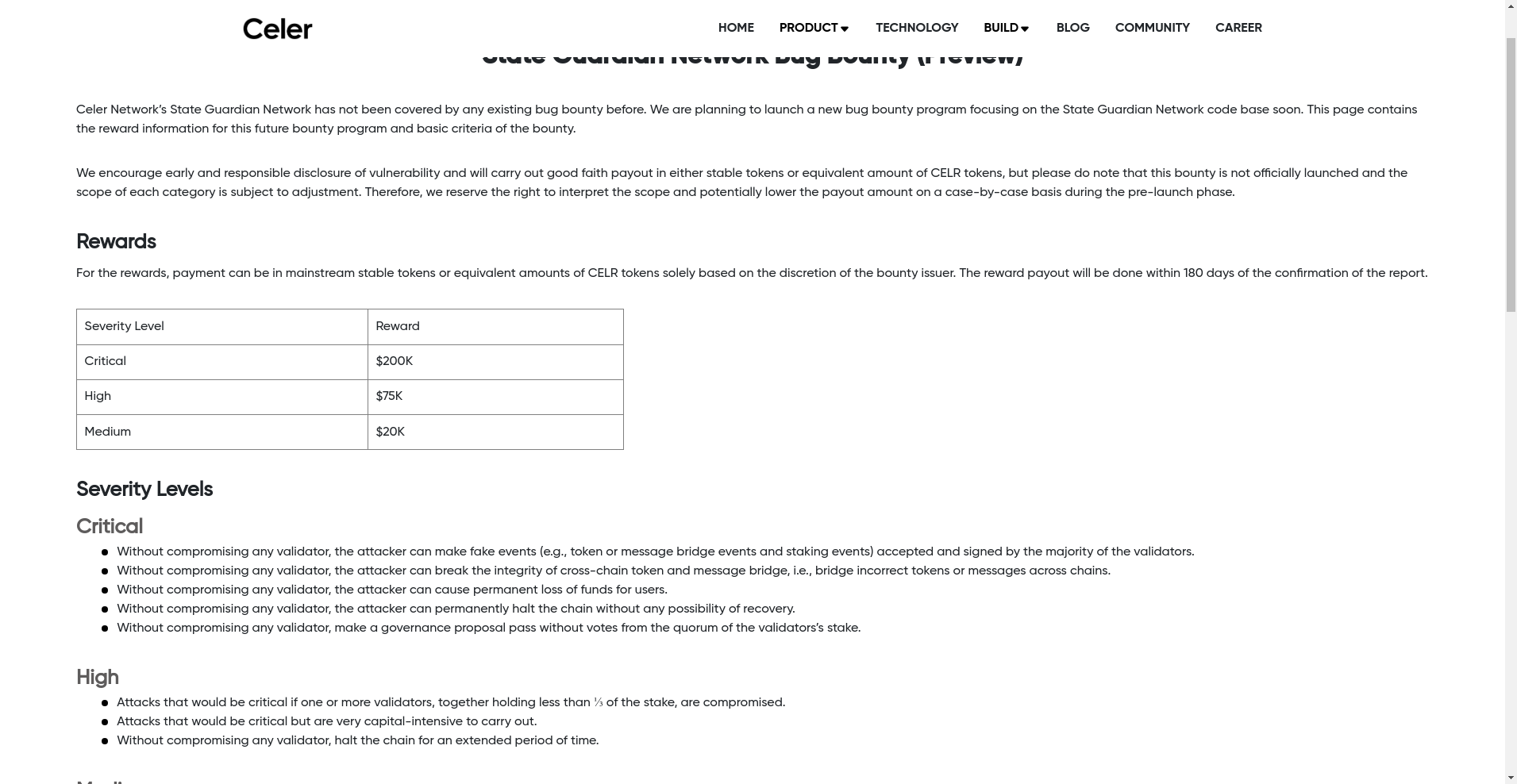
Assessing the Security and Integrity of Celer Network
The security analysis is primarily based on Cer.live platform data and publicly available audit reports. The platform reports a platform audit by Certik (a leading security auditor), with expertise in blockchain security, indicating a baseline of security review. The Celer platform underwent audit coverage with a score of 30% visibility, signifying that detailed review procedures might be ongoing or incomplete.
The Cer.live report notes that incidents exist within the platform but does not specify critical vulnerabilities or exploit risks directly impacting end-users. However, one notable security aspect is the ongoing bug bounty program, including a dedicated initiative for the State Guardian Network (SGN), with rewards up to $200,000 for critical vulnerabilities. This high bounty indicates an active effort to secure the protocol’s core components against sophisticated attacks.
Key technical details from available audits highlight:
- Presence of bugs or incidents suggests some ongoing security challenges, but no publicly reported exploits demonstrate immediate danger.
- Only one platform audit from Certik, which calls for ongoing security vetting and transparency.
- Bug bounty programs serve as a critical mechanism for incentivizing external audits of code vulnerabilities.
- User funds and cross-chain assets depend heavily on the security effectiveness of bridges and messaging protocols.
While the audit and bounty programs point to reasonable security measures, the complexity of cross-chain bridges inherently introduces risks—such as smart contract bugs, misconfigurations, or validator attacks—that should be carefully considered by potential investors or users.
A Breakdown of Celer Network Tokenomics
The native token $CELR has a total supply of 10,000,000,000 tokens, with circulating supply roughly 5.6 billion tokens. Its market cap fluctuates around ~$56.7 million, with a recent low-price of approximately $0.010 and significant trading volume (~$4.2 million), indicating active, albeit modest, market engagement.
Token utility includes:
- Governance participation through proposal voting.
- Staking to secure network operations, especially within the State Guardian Network (SGN).
- Incentivization of liquidity providers for cBridge.
- Potential utility within dApps built on Celer IM, facilitating asset transfer and message passing.
Token distribution details highlight allocations to the team, investors, and community treasury, with vesting schedules to align incentives. The available data suggest an economic model centered on utility-driven token demand, but with clear risks of inflation or market volatility if demand wanes.
Potential risks for holders include market liquidity constraints, dependency on continued development, and security of the underlying smart contracts governing token staking and utility.
Assessing Celer Network's Development and Ecosystem Activity
Community summaries and audit links indicate an active development environment, with various integrations supporting demonstrated use cases. Notably, the efforts include multiple chain support, security upgrades, and community proposals to improve functionality.
The recent focus has been on expanding chain support—such as Oasis Sapphire, Filecoin FVM, and others—and enhancing cross-chain messaging capabilities with Celer IM. The ongoing bug bounty initiatives and active community proposals reflect a healthy innovation pipeline.
Such activity showcases a project rooted in continuous development, aiming to adapt swiftly to emerging blockchain trends. However, distinguishing genuine progress from marketing claims requires scrutiny of on-chain metrics and real-world use cases.
Real-world traction includes:
- Active cross-chain transfers on cBridge across multiple networks.
- Development of new interoperability standards and SDKs for developers.
- Community governance proposals reflecting decentralized decision-making.
Reviewing the Terms and Conditions
The project's legal documentation—accessible via standard privacy and terms links—appears comprehensive, covering user rights and platform obligations. No unusual or risky clauses are explicitly evident in the publicly available documentation.
The bug bounty terms explicitly state that investigations are confined to the platform’s codebase, with restrictions on testing activities (e.g., no testing on mainnets or with exploits like DoS or social engineering). This indicates adherence to responsible disclosure policies, reducing risks of misuse during security evaluations.
Final Analysis: The Investment Case for Celer Network
Celer Network presents itself as a technically robust multi-chain interoperability platform, backed by a highly qualified team and a broad ecosystem of supported chains and tokens. Its flagship products—cBridge and Celer IM—are actively deployed, with ongoing security audits and community involvement through forums and bug bounty programs.
However, inherent risks in cross-chain bridges—such as smart contract vulnerabilities, validator attacks, and liquidity risks—cannot be dismissed. The relatively modest market cap and price point suggest limited liquidity and adoption at present, which could influence long-term viability.
Pros / Strengths
- Strong technical foundation with credible team members from leading academic and industry institutions.
- Broad interoperability supporting 45+ chains and 175 tokens, indicating extensive ecosystem integration.
- Active security posture backed by Certik audits and ongoing bug bounty programs.
- Continuous product development and ecosystem expansion, demonstrating commitment to innovation.
- Decentralized governance proposals, fostering community involvement.
Cons / Risks
- Limited transparency of comprehensive audit reports, with only Certik audit publicly available.
- Security risks inherent in cross-chain bridges—smart contract bugs, validator collusions, or exploits could threaten user assets.
- Market liquidity and adoption levels remain relatively low, possibly affecting token value and network utility.
- Potential for development delays or technical failures impacting ecosystem reliability.
- Dependence on external oracles and third-party integrations, which complicate security guarantees.
In conclusion, Celer Network's technology and community activity suggest a credible project capable of significant impact in blockchain interoperability. Yet, investors and users should remain vigilant about the always-present technical, security, and market risks associated with cross-chain solutions. Sound due diligence and monitoring of ongoing audits and community governance are recommended before engagement.

Olivia Lewis
Sociotechnical Systems Analyst
I analyze the intersection of social networks and blockchain systems. I use data to expose how scammers manipulate communities with bots, FUD, and engineered hype.
Similar Projects
-
Bomb Shelter Inu (BOOM)
In-Depth Review of Bomb Shelter Inu (BOOM) Crypto Project | Scam Checker & Risk Analysis
-
Momo Token
Comprehensive Review of Momo Token: Crypto Scam Checker & Project Analysis
-
Tokabu Art
Review of Tokabu Art: Is This Crypto Project a Scam or Legit? | Crypto Scam Checker
-
EBM Avenue
In-Depth EBM Avenue Review: Is This Crypto Project a Scam or Legit? | Crypto Scam Checker
-
Enjin Coin
Enjin Coin Review: Scam Check & Legitimacy Analysis